Ransomware is one of the most insidious types of malware on the internet. It sneaks onto your system, secretly encrypts your files and then demands a Bitcoin payment in return for giving you the unlock key. Even then, there is absolutely no guarantee that the hacker will unlock your files even if you pay.
Ransomware is an increasing threat to computer users, especially those who run small businesses. Smaller enterprises are being targeted specifically because they don’t usually have in-house IT support or the resources for advanced network and malware protection. That means you have to be even more vigilant than usual to prevent being infected.
Here at Dave’s Computers, we get to see many ransomware attacks. Usually the first thing you notice is your computer running slightly slower than usual. Many users don’t even notice that. Often, the first thing you see is a notice in the center of your screen telling you that your files have been encrypted and that you need to send x amount of dollars to a Bitcoin account to get the key to unlock them. It is not a nice feeling when you see these notices I can tell you.
Types of ransomware
Ransomware comes in three main flavors, scareware (yes really), encryption ransomware and lockout ransomware. Each is annoying and uses a slightly different attack to do their work.
Scareware – Scareware are those fake IT support notifications that pop up or fake virus reports that can appear on your desktop. These work because a piece of malware including popups is installed and once you click on the notification, it allows the ransomware itself to be downloaded. There isn’t always an extra piece though, sometimes you are just ‘encouraged’ to call a number to receive specialist support.
Encryption ransomware – Encryption ransomware is the most popular and the one I described above. It will install without your knowledge and encrypt your files while remaining undetected. A particular observant user may notice their system running slightly slower than usual but the majority of users wouldn’t notice.
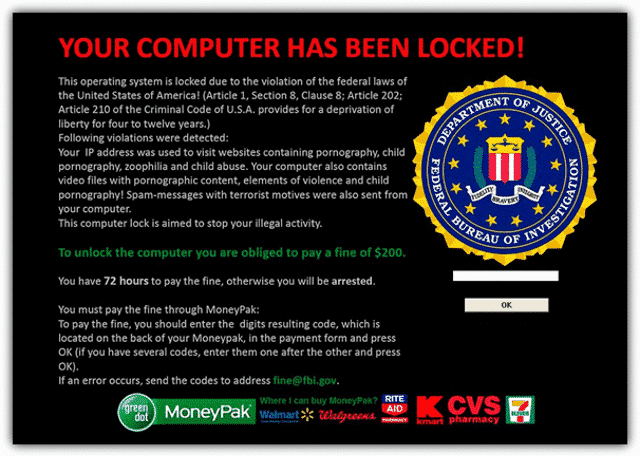
Lockout ransomware – Lockout ransomware shows a screensaver that can purport to be from the FBI or Department of Justice telling you that there has been illegal activity detected and you must pay a fine. It’s obviously fake. While the government does like to snoop, this isn’t how they operate and they are more likely to come knocking on your door than locking your computer down.
How ransomware is delivered
The one positive thing about ransomware is that is needs manual intervention to activate. It is usually delivered via email masquerading as a legitimate notice, invoice or something like that. It tricks the user into opening it up to do its work. The ransomware will secretly install and encrypt your files before showing you that notice.
The positive is that if you educate your users against this kind of threat and use effective email filters, you can avoid the vast majority of ransomware threats.
How to avoid ransomware
The best defense for any IT network is defense in depth. That means using a hardware firewall, email scanning, antivirus and malware detection. It also includes employee education and restricting user privileges too. As mentioned earlier, the main attack vector for ransomware needs some kind of human action to activate. If you can remove that action as much as possible, the chances of a successful attack are much lower.
A hardware firewall is the most basic protection and something we think is an essential part of any small business security setup. Cloud malware scanning is become more effective and more popular. If you can afford it, we would definitely suggest using some kind of barrier defense. Cloud scanning means the malware never even reaches your network, which is worth the cost alone.
Running a good antivirus solution locally is next. Make sure it has active monitoring and will automatically detect and remove any suspicious attachments or code. A malware scanner is also useful. Have them both set to automatically update and scan user’s computers on a regular basis to ensure maximum protection.
Most email systems can be configured to automatically remove web links, attachments and code contained within emails too. This is a good security measure but may get in the way of productivity. Despite that, it is a good precaution to take if your mail system will support it.
User education is probably the most effective method to protect your network from ransomware. Even if you have all of these physical protections in place, some malware will get through. Most malware writers use social engineering to con people into opening the message or clicking the link. Some of these tricks are very sophisticated and can fool all but the most aware users.
Teaching users to never open mails if they don’t know who sent it, never open attachments unless they have asked for them or don’t know the sender will all help. As will not following email links unless you know the sender. Having security high on your priority list will go a long way to preventing you becoming a victim.
Finally, restricting user machine privileges can also help. It is controversial as users don’t usually like not being able to do something on the computer they use, but it is a very effective security measure. If an employee cannot make changes to files, neither than the ransomware. Conversely, if the user has admin privileges, so will the malware and both will be able to do what they like on your network with predictable results!
I dislike ransomware. While I don’t particularly like any malware, this version is dark, mean and shows the worst of people. Don’t become a victim. Use the tips in this guide to bolster your physical defenses and educate your users. It will go a long way to avoiding the worst of these risks.
This threat management guide from Computer Weekly has some useful information too. This cautionary tale bears some scrutiny too.
If you need help with your IT security or data recovery as a result of a malware attack, contact Dave’s Computers today. We are here to help!